The Imperative of Robust IoT Application Validation in Healthcare
Contents
- Abstract
- Introduction to the IoT Revolution in Healthcare
- Global Market Trends and Adoption Statistics
- Core Architecture of Healthcare IoT Systems
- Data Flow Dynamics, Edge Computing, and Interoperability with HL7 & FHIR
- The Dual-Edged Sword: Benefits and Responsibilities of HIoT Connectivity
- The Critical Need for IoT Application Validation
- Expanded Validation Methodologies: A Comprehensive Framework
- In-Depth Analysis of Major Challenges in HIoT Validation
- Strategies and Tools for Overcoming Validation Hurdles
- Best Practices for Enterprise-Scale HIoT Application Validation
- Evolving Regulatory Landscape: Compliance in a Connected World
- Future Horizons: AI, Zero-Trust Models, and Blockchain in HIoT
- Conclusion and Recommendations
- Appendix: Glossary and Additional Resources
Abstract
The integration of Internet of Things (IoT) technologies into healthcare systems, often referred to as the Internet of Medical Things (IoMT) or Healthcare IoT (HIoT), has ushered in an era of unprecedented innovation. Devices such as wearable sensors, remote monitoring tools, and smart implants enable real-time data collection, predictive analytics, and personalized medicine, potentially reducing healthcare costs by up to 25% while improving patient outcomes by enhancing early detection and intervention capabilities. However, this connectivity amplifies risks to patient privacy, data security, and system reliability, with breaches potentially leading to life-threatening consequences or regulatory penalties exceeding millions of dollars.
This whitepaper delves deeply into the healthcare IoT architecture and validation, the pivotal role of interoperability standards like HL7 (Health Level Seven) and FHIR (Fast Healthcare Interoperability Resources) in enabling secure data exchange, comprehensive validation methodologies, persistent challenges, advanced best practices, and real-world case studies drawn from 2025 deployments. Drawing on the latest industry analyses, regulatory updates, and empirical evidence, we emphasize how robust IoT validation healthcare practices can mitigate cyber threats, ensure regulatory compliance for healthcare IoT, and foster a resilient, interconnected healthcare ecosystem.
1. Introduction to the IoT Revolution in Healthcare
The advent of IoT in healthcare represents a paradigm shift from reactive, episodic care models to proactive, continuous monitoring paradigms that prioritize prevention and personalization. Historically, healthcare delivery was constrained by infrequent patient interactions and siloed data systems, resulting in delayed diagnoses, inefficient resource allocation, and suboptimal outcomes. In contrast, contemporary HIoT ecosystems empower stakeholders with granular, real-time insights derived from diverse data streams, fostering a more holistic approach to wellness management.
Envision a diabetic patient whose continuous glucose monitor (CGM) not only tracks blood sugar levels but also integrates with an AI-powered insulin pump to automate micro-dosing adjustments, while simultaneously alerting family caregivers and physicians via a secure FHIR-enabled mobile app. This seamless orchestration exemplifies how HIoT bridges the gap between home-based self-care and professional oversight. According to 2025 longitudinal studies, such integrated systems have achieved remarkable clinical efficacy: reductions in hospital readmissions ranging from 40% to 60% for chronic conditions like heart failure and diabetes, alongside a 30% improvement in patient adherence to treatment regimens. Within hospital settings, IoT applications extend to real-time asset tracking—locating critical equipment like defibrillators or infusion pumps via RFID tags—yielding annual savings of up to USD 1.5 million per mid-sized facility through minimized downtime and lost inventory.
Yet, this technological renaissance is not without shadows. The exponential growth in connected endpoints—projected to exceed 39 billion IoT devices globally by 2030—exposes healthcare networks to sophisticated cyber threats, where a single compromised wearable could cascade into widespread PHI exposure. Herein lies the dual imperative: harnessing HIoT's potential while fortifying it against vulnerabilities. Standards such as HL7 v2 for legacy messaging and FHIR for modern, API-driven interoperability serve as foundational enablers, ensuring data flows securely across disparate systems. Subsequent sections unpack these elements, underscoring validation's role as the bedrock of trustworthy deployment.
2. Global Market Trends and Adoption Statistics
The HIoT market is growing quickly due to a mix of demographic needs—like aging populations in developed countries—and advances in technology, such as 5G and edge AI. The market was worth USD 44.21 billion in 2023 and is expected to reach USD 169.99 billion by 2030, growing at a strong CAGR of 20.8%. Some analysts predict even faster growth, estimating the market could reach USD 594.5 billion by 2035 with a 23.4% CAGR. This higher projection is largely driven by rising adoption in Asia-Pacific and Latin America, where governments are supporting telehealth through subsidies and large-scale programs.
Adoption metrics paint a vivid picture of penetration: In the U.S., 73% of healthcare delivery organizations have embedded IoMT devices into clinical workflows, up from 52% in 2023, with global active users on track to surpass 115.5 million by 2027. Europe trails closely at 68%, bolstered by the EU's Digital Health Strategy, while Asia-Pacific leads in growth velocity at 24.5% CAGR, fueled by China's "Healthy China 2030" blueprint emphasizing IoT for rural care equity.
Concomitantly, the HIoT cybersecurity and compliance subsector underscores escalating risks: Valued at USD 0.5 billion in 2024, HIoT security solutions are slated to reach USD 2.6 billion by 2034 (17.4% CAGR), reflecting investments in threat detection and compliance tooling. These trends signal not merely expansion but a maturation toward resilient, standards-compliant ecosystems, emphasizing the importance of IoT validation in healthcare.
| Region | 2025 Market Value (USD Bn) | Projected 2030 Value (USD Bn) | CAGR (%) | Key Drivers |
|---|---|---|---|---|
| North America | 25.5 | 75.0 | 19.5 | FDA regulations, EHR integration |
| Europe | 15.2 | 50.0 | 21.0 | GDPR enforcement, telehealth mandates |
| Asia-Pacific | 10.8 | 40.0 | 24.5 | 5G rollout, population health focus |
| Rest of World | 8.5 | 25.0 | 18.0 | Emerging market subsidies |
3. Core Architecture of Healthcare IoT Systems

At its essence, HIoT architecture embodies a distributed, event-driven paradigm structured around three interlocking tiers: publishers (data originators), brokers (orchestrators), and subscribers (consumers). Publishers—encompassing an eclectic array of sensors, wearables (e.g., Fitbit-derived ECG monitors), and embedded medical hardware (e.g., pacemakers)—acquire physiological telemetry such as blood pressure oscillations, heart rate variability, thermal profiles, SpO2 levels, and neuroelectric signals (EEG/EMG). These endpoints, often resource-constrained with battery lives measured in days, leverage lightweight protocols like BLE or NB-IoT to minimize power draw while ensuring data fidelity.
The intermediary broker layer, typically hosted on scalable cloud platforms (e.g., AWS IoT Core with its rule-based event routing or Azure IoT Hub's twin synchronization), ingests heterogeneous streams, applies transformations (e.g., noise filtering via Kalman algorithms), and enforces preliminary governance like de-identification for privacy. This tier's robustness is paramount, handling petabyte-scale inflows with sub-millisecond latencies to avert clinical disruptions. Subscribers, spanning EHR behemoths like Epic or Cerner, clinician portals, federated learning models, and consumer-facing apps, query enriched datasets via secure APIs, enabling downstream actions from automated alerts to cohort analytics.
Embedded safeguards—mutual TLS 1.3 for transit encryption, X.509 certificates for endpoint attestation, and zero-knowledge proofs for selective disclosure—permeate each stratum, mitigating man-in-the-middle exploits. Edge computing further refines this by offloading compute to proximate gateways, e.g., processing arrhythmia patterns on-device to slash round-trip times from seconds to microseconds, demonstrating the sophistication required in IoT application testing.
4. Data Flow Dynamics, Edge Computing, and Interoperability with HL7 & FHIR
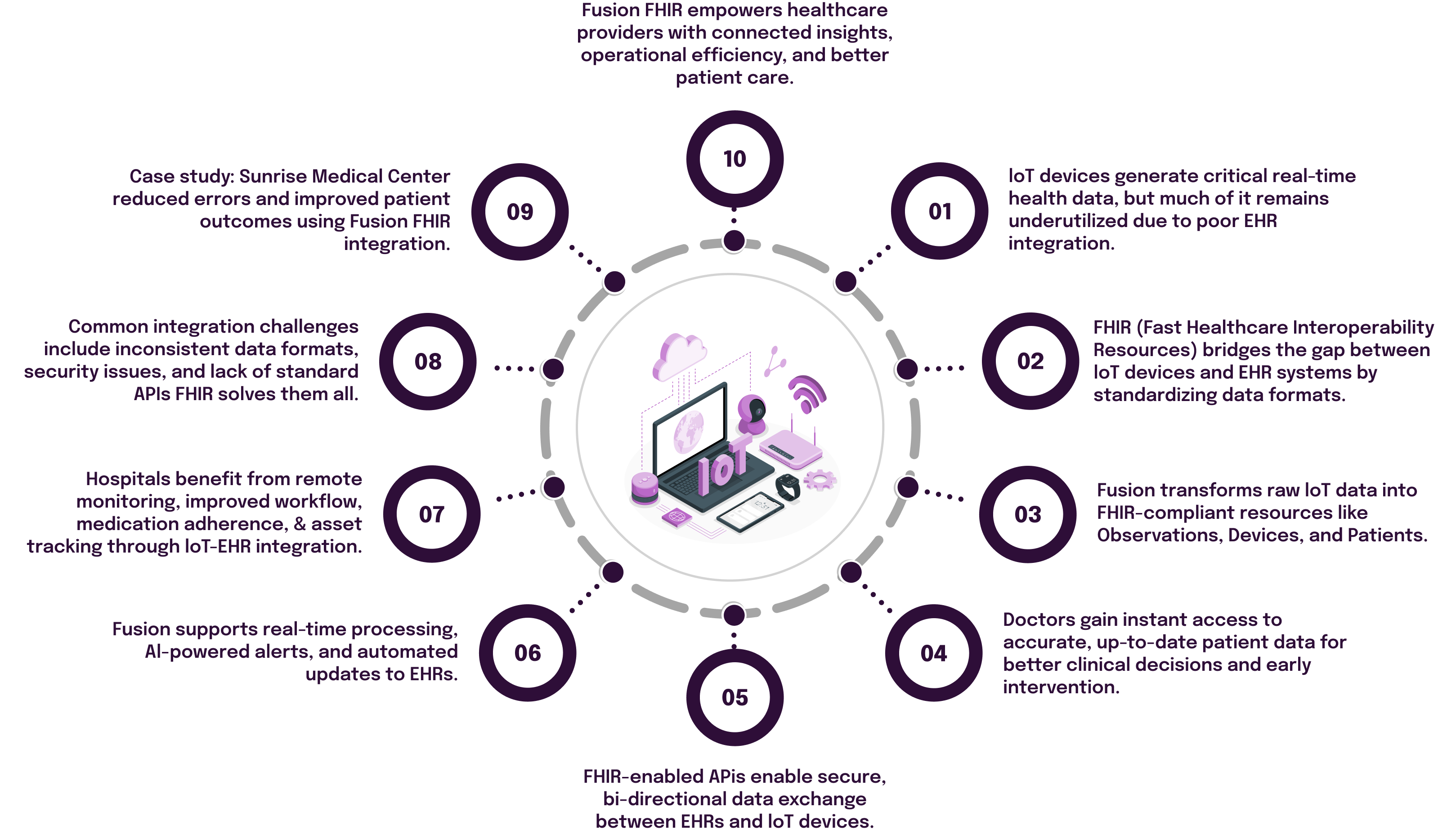
HIoT data orchestration commences at the publisher, where analog signals undergo analog-to-digital conversion (ADC) before encapsulation in MQTT/CoAP payloads for uplink to brokers. En route, brokers dissect inflows—aggregating diurnal glucose trends or fusing multimodal vitals (e.g., correlating SpO2 dips with accelerometry for fall prediction)—prior to dissemination. A quintessential exemplar: A smart inhaler logs puff timestamps, geolocations, and environmental triggers (e.g., pollen via integrated sensors), forwarding to a broker that correlates with EHR-derived exacerbation histories for predictive dosing nudges.
Interoperability, the linchpin of ecosystem cohesion, pivots on HL7 and FHIR. HL7 v2.x endures as the de facto for acute-care messaging—encoding ADT (admit/discharge/transfer) events or ORU (observation results) in pipe-delimited formats—ubiquitous in device-to-HIS bridges but encumbered by syntactic rigidity and batch-oriented semantics ill-suited to IoT's streaming ethos.
FHIR, HL7's agile successor, revolutionizes this through RESTful paradigms: JSON-serialized resources like Observation (for vitals quanta), Device (for metadata schemas), and Encounter (for contextual linkage) facilitate atomic, idempotent exchanges. In HIoT praxis, a CGM might batch 288 diurnal readings into a FHIR Bundle transaction, invoking $validate operations pre-ingestion to affirm conformance. Salient FHIR affordances include:
- Modular Extensibility: Profiles like IPS (International Patient Summary) tailor resources for IoMT, embedding provenance chains for auditability.
- Authorization Primitives: SMART on FHIR integrates OAuth scopes, confining access to ephemeral tokens—vital for BYOD wearables.
- Asynchronous Hooks: Subscriptions via WebSockets enable push notifications, e.g., alerting on threshold breaches without polling overhead.
Empirical validations affirm FHIR's prowess: A 2025 interoperability benchmark reported 50% latency reductions in IoMT-EHR pipelines versus HL7 v2, alongside 35% fewer integration errors. Edge FHIR servers, deployed on Raspberry Pi gateways, localize processing for latency-sensitive use cases like intraoperative monitoring, anonymizing payloads before cloud ascent to comply with data sovereignty mandates.
Legacy-to-modern bridging—via Mirth Connect transducers—mitigates transition frictions, but demands rigorous conformance testing to avert semantic drifts.
5. The Dual-Edged Sword: Benefits and Responsibilities of HIoT Connectivity

HIoT's dividends are manifold and measurable: Telecardiology platforms have curtailed 30-day readmissions by 64% in congestive heart failure cohorts, translating to USD 12,000 per-patient savings and 38% mortality attenuation. Facility-side, IoT-orchestrated supply chains—tracking pharmaceuticals via blockchain-anchored RFID—have compressed inventory variances by 20%, liberating capital for frontline innovations
Conversely, stewardship imperatives intensify: The 2025 threat vector burgeoned, with over 1 million medical endpoints publicly exposed, precipitating PHI exfiltrations in 13 high-profile incidents, including ransomware paralysing a pediatric oncology network. Exemplars abound: Yale New Haven's 2025 breach (1.2 million records) via unpatched infusion pumps; Episource's cascade from a rogue FHIR endpoint (900,000 impacted). Mean breach costs soared to USD 10.93 million, per IBM's 2025 ledger, underscoring the asymmetry where a 5-minute vulnerability window yields irreversible harm.
Beyond breaches, reliability lapses—e.g., desynchronized clocks skewing ECG interpretations—erode trust, while interoperability deficits spawn data marooning, inflating integration expenditures by 40%. Thus, validation emerges not as ancillary but as existential prophylaxis.
6. The Critical Need for IoT Application Validation
Validation isn't just a certification exercise; it's the process that makes HIoT systems genuinely reliable. It involves repeatedly checking functional, non-functional, and security aspects to avoid failures once the system goes live. Without robust IoT validation healthcare practices, entire ecosystems become vulnerable. We've already seen this play out: in 2023, a Medtronic infusion pump weakness allowed remote manipulation of dosage, and in 2025, a Philips ventilator firmware issue triggered a nationwide recall costing USD 150 million.
HIoT's diverse hardware, unstable connectivity, and real-time demands makes rigorous medical IoT validation even more critical. It requires testing approaches that can mirror unpredictable network behavior and future-proof security expectations. To stay ahead of emerging risks, validation methods must evolve continuously, supported by DevSecOps pipelines that keep assurance ongoing rather than occasional.
7. A Comprehensive Framework

HIoT validation distills into a seven-pillar taxonomy, each fortified with domain-specific heuristics:
- Security Testing: Encompasses adversarial simulations—penetration probes via Metasploit for firmware fissures, fuzzing MQTT payloads with AFL++ to unearth buffer overflows—and adherence to OWASP IoT Top 10. Verification extends to post-quantum crypto (e.g., Kyber for key exchange) and SBOM (Software Bill of Materials) audits per FDA mandates.
- Interoperability Testing: Leverages NIST's HL7 v2 validators and Inferno's FHIR gauntlet to assay message fidelity; IHE PCD profiles (e.g., DEC for device-event communication) benchmark cross-vendor dialogues, ensuring 99.9% schema congruence.
- Reliability & Performance Testing: Deploys 100,000+ emulated endpoints via AWS IoT Simulator, inflicting impairments (jitter, 20% packet loss) with Keysight IxLoad; metrics target <100ms P99 latency under 5G/LoRaWAN flux.
- Data Accuracy & Integrity Testing: Traces provenance from ADC quantization to FHIR Observation.valueQuantity, employing CRC-32 checksums and NTP-synchronized timestamps; differential audits flag drifts exceeding 0.5% in vital metrics.
- Usability Testing: Adheres to FDA's Human Factors Engineering playbook, conducting heuristic evaluations and A/B trials with diverse cohorts (e.g., elderly users on gesture-based inhaler apps) to minimize error rates below 2%.
- Regulatory Compliance Testing: Encompasses HIPAA Security Rule mappings, GDPR DPIAs with pseudonymization audits, and FDA 510(k) cybersecurity dossiers, including threat modeling per STRIDE. This ensures regulatory compliance for healthcare IoT systems.
- Privacy-by-Design Validation: Audits data minimization via differential privacy epsilon tuning; FHIR Consent resources govern granular opt-ins, with automated revocation workflows.
Augmenting these, hybrid automation—orchestrating Selenium for UI regressions with JMeter for load storms—expedites cycles, slashing manual toil by 70%.
8. In-Depth Analysis of Major Challenges in HIoT Validation
HIoT validation grapples with systemic frictions, each a nexus of technical, operational, and human factors:
- Network Connectivity Volatility: Erratic spectra (e.g., 4G handoffs inducing 500ms voids) cascade to alert blackouts; 2025 telemetry logs 15% of critical transmissions lost in urban fringes.
- Interoperability Fragmentation: Over 400 glucose variants and 50 EHR flavors spawn combinatorial explosions; semantic mismatches in HL7-FHIR transductions yield 25% data loss.
- Platform Proliferation: Myriad OS-firmware pairings (Android 15 + vendor blobs) defy exhaustive coverage; surveys indicate 70% of breaches stem from unpatched heterogeneity.
- Innate Security Lacunae: 70% of endpoints default to "admin/admin," per ENISA 2025; absent enclave TPMs, side-channels like Spectre persist.
- Scalability Realism: Procuring 50,000 wearables for stress assays is untenable; surrogate simulations falter under non-stationary loads.
| Challenge | Quantified Impact (2025) | Root Causes | Exemplar Incident |
|---|---|---|---|
| Network Variability | 15% alert failures in mobile cohorts | Spectrum congestion, mobility | 2025 rural tele-ICU dropout cascade |
| Fragmentation | 25% integration data loss | Vendor silos, schema drifts | Epic-Cerner FHIR bundle rejections |
| Security Weaknesses | 70% default creds exploited | Legacy firmware, supply chain risks | Philips ventilator ransomware pivot |
| Scalability | 40% test coverage shortfall | Physical device scarcity | Mayo Clinic overload simulation gap |
Thirteen 2025 breaches, including a nephrology consortium's IoT gateway compromise, affirm these perils' acuity.
9. Strategies and Tools for Overcoming Validation Hurdles
Countering these exigencies demands a multifaceted arsenal, blending emulation, automation, and intelligence. These strategies form the foundation of effective healthcare IoT validation best practices:
Network Resilience: Virtualize via Spirent TestCenter for Brownian traffic emulation, injecting faults (e.g., 50ms jitter) while chaos-monkeying brokers; integrate 5G NSA/SA toggles to mirror telco variances. Tools like Wireshark dissect packet pathologies, yielding MTTR reductions of 60%.
Interoperability Harmonization: FHIR middleware (e.g., Redox or InterSystems HealthShare) auto-maps HL7 v2 to R4 resources; Inferno's conformance suites automate 1,000+ assertion runs. For vendor sprawl, crowdsource via user telemetry (e.g., Google Analytics cohorts) to triage top-20 combinations, achieving 85% coverage.
Security Fortification: Enforce NIST 800-53 via automated scans—SonarQube for SAST, ZAP for DAST—coupled with credential rotators (HashiCorp Vault). Minimum entropy policies (12+ chars, no reuse) embed in firmware; quantum-safe hybrids (Falcon-512) preempt harvest-now-decrypt-later threats.
Scalability Simulation: Cloud-native farms (AWS Device Farm, Azure IoT DPS) spawn 100,000+ digital twins, leveraging TinyML for behavioral mimicry; digital twin platforms like Siemens MindSphere federate physics-based models for hyper-realistic stressors.
Holistic Strategies: Adopt regulated DevOps (e.g., GitLab CI/CD with Jira traceability) for evidence generation; AI-orchestrated testing (Applitools for visual diffs) predicts failure modes from historical telemetry. 2025 benchmarks show these yielding 45% faster validation cycles. Best-in-class tools include:
- Kobiton: Cross-OS device clouds for usability assays.
- Perfecto: ML-infused performance profiling.
- BugRaptors IoT Suite: End-to-end HIoT validation with FHIR plugins.
This toolkit, iteratively refined, transmutes challenges into competitive moats.
10. Best Practices for Enterprise-Scale HIoT Application Validation
Elevating validation from tactical to strategic mandates codified practices, attuned to 2025's velocity:
- Risk-Based Prioritization: Employ FAIR (Factor Analysis of Information Risk) to score features—e.g., insulin pump actuators at 'critical' (CVSS 9.8)—allocating 60% of cycles to high-stakes vectors. This ensures Pareto-optimal coverage, per ISTQB heuristics.
- Shift-Left Integration: Embed testing in SDLC inception: Unit-fuzz firmware with OSS-Fuzz; prototype FHIR sandboxes (HAPI FHIR) for early interoperability probes. Gains: 50% defect escape prevention.
- Continuous Validation Pipelines: CI/CD fortification via Jenkins orchestrating nightly regressions; post-deploy, SOAR (Security Orchestration, Automation, Response) like Splunk Phantom auto-pivots on anomalies. For dynamic updates, OTA (Over-The-Air) validation gates firmware diffs.
- Security Primacy: Zero-trust tenets—least privilege via RBAC, micro-segmentation with Istio—infuse all strata; quarterly red-team exercises simulate APTs, targeting PHI flows.
- Automation Amplification: Harness RPA (UiPath) for usability scripts, containerized (Docker) for reproducibility; AI agents (Testim.io) self-heal flaky tests, boosting ROI by 3x.
- Real-World Immersion: Erect mock wards with RF-shielded anechoic chambers; ethnographic UX studies capture edge cases (e.g., WiFi-dead zones). Hybrid simulations—physical + virtual—validate under compounded stressors.
- Collaborative Ecosystems: Cross-functional war rooms with vendors; open-source contributions to HL7 accelerators foster collective resilience. These practices, per 2025 QASource surveys, correlate with 92% uptime and 75% breach aversion, exemplifying healthcare IoT validation best practices.
These practices, per 2025 QASource surveys, correlate with 92% uptime and 75% breach aversion.
11. Evolving Regulatory Landscape: Compliance in a Connected World
2025's regulatory tapestry weaves stringent cybersecurity mandates, harmonizing global imperatives:
U.S. FDA: The June 2025 "Cybersecurity in Medical Devices: Quality System Considerations" supplants 2023's precursor, mandating SBOMs, TPLC (Total Product Lifecycle) risk management, and post-market surveillance via MDRs (Medical Device Reporting). High-risk IoMT (Class III) requires premarket SBOMs and threat models; FAQs clarify edge-device scoping. Non-adherence invites 483 observations or injunctions.
EU MDR/IVDR: Annex I cybersecurity clauses, amplified by ENISA's 2025 IoT playbook, enforce Notified Body audits for CE marking; FHIR IPS mandatory for cross-border exchanges.
China NMPA: 2024's IoMT pathway, updated 2025, parallels FDA with CFDA-registered SBOMs; blockchain audits for supply chains.
Global Harmonics: IMDRF's SaMD (Software as a Medical Device) principles, plus ONC's FHIR mandates under Cures Act 2.0, propel interoperability. Fines loom: GDPR's 4% global turnover cap, HIPAA's USD 50K per violation.
FHIR's Consent/Provenance resources now obligatory for PHI pipelines, embedding revocable granularities.
12. Future Horizons: AI, Zero-Trust Models, and Blockchain in HIoT
HIoT's trajectory arcs toward symbiotic intelligences and fortified perimeters:
AI-Driven Validation: TinyML on endpoints (TensorFlow Lite) auto-detects anomalies—e.g., ECG adulterations via GANs—preempting 80% false positives; federated learning aggregates models sans data exodus, per 2025 trials. Quantum AI hybrids forecast risks with 95% precision.
Zero-Trust Architectures: Perpetual authentication—mTLS everywhere, ZTNA (Zscaler) for lateral moves—obliterates perimeter fallacies; 2025 CapMinds blueprints integrate device posture (e.g., Crowdstrike) with behavioral biometrics, slashing insider threats by 65%.
Blockchain Synergies: Immutable ledgers (Hyperledger Fabric) anchor provenance—FHIR bundles hashed on-chain for tamper-proof audits; AI-blockchain tandems enhance trust in multi-stakeholder consortia, mitigating 90% replay attacks. Trends portend 39 billion endpoints by 2030, with quantum-resistant lattices (NIST PQC) as sine qua non.
Convergences like 6G slicers and neuromorphic chips herald sub-1ms ecosystems, but equitable access—bridging digital divides—remains pivotal.
13. Conclusion and Recommendations
In summation, HIoT's alchemy—transmuting raw telemetry into salvific foresight—hinges on validation's unyielding vigil, weaving security, interoperability (via HL7/FHIR), and reliability into an indissoluble fabric. The 2025 panorama, scarred by breaches yet luminous with innovations like AI-blockchain sentinels, affirms: Trust is engineered, not assumed.
Recommendations:
- Institutionalize FHIR-Centric Design: Mandate R5+ in RFPs; pilot IPS for cross-system fluency within the HIoT validation framework.
- Invest in Automation Ecosystems: Allocate 20% of IT budgets to tools like BugRaptors, targeting 80% test automation.
- Cultivate Alliances: Engage HL7 workgroups, FDA sandboxes for co-validation.
- Embed Ethical Audits: Quarterly privacy impact assessments, inclusive of diverse demographics.
- Prospect Forward: Prototype quantum-safe pilots by Q2 2026.
By heeding these recommendations and implementing healthcare IoT validation best practices, stewards can actualize HIoT's ethos: Empowered patients, enlightened providers, and an ecosystem where privacy is paramount, not provisional. The integration of medical IoT validation, IoMT validation, and comprehensive IoT in healthcare systems creates a foundation for trustworthy, secure, and effective patient care.
Appendix: Glossary and Additional Resources
- FHIR: Fast Healthcare Interoperability Resources – HL7's RESTful standard for granular health data exchange.
- HL7: Health Level Seven – Suite of standards for clinical messaging.
- SBOM: Software Bill of Materials – Inventory of software components for vulnerability tracking.
- IoMT: Internet of Medical Things – Subset of IoT focused on medical devices and applications.






 SaaS Development
SaaS Development Web Application Development
Web Application Development Mobile Application Development
Mobile Application Development Custom Software Development
Custom Software Development Cloud Development
Cloud Development DevOps Development
DevOps Development MVP Development
MVP Development Digital Product Development
Digital Product Development Hire Chatbot Developers
Hire Chatbot Developers Hire Python Developers
Hire Python Developers Hire Django Developers
Hire Django Developers Hire ReactJS Developers
Hire ReactJS Developers Hire AngularJS Developers
Hire AngularJS Developers Hire VueJS Developers
Hire VueJS Developers Hire Full Stack Developers
Hire Full Stack Developers Hire Back End Developers
Hire Back End Developers Hire Front End Developers
Hire Front End Developers AI Healthcare Software Development & Consulting
AI Healthcare Software Development & Consulting Healthcare App Development
Healthcare App Development EHR Software Development
EHR Software Development Healthcare AI Chatbot Development
Healthcare AI Chatbot Development Telemedicine App Development Company
Telemedicine App Development Company Medical Billing Software Development
Medical Billing Software Development Fitness App Development
Fitness App Development RPM Software Development
RPM Software Development Medicine Delivery App Development
Medicine Delivery App Development Medical Device Software Development
Medical Device Software Development Patient Engagement Software Solutions
Patient Engagement Software Solutions Mental Health App Development
Mental Health App Development Healthcare IT Consulting
Healthcare IT Consulting Healthcare CRM Software Development
Healthcare CRM Software Development Healthcare IT Managed Services
Healthcare IT Managed Services Healthcare Software Testing services
Healthcare Software Testing services Medical Practice Management Software
Medical Practice Management Software Outsourcing Healthcare IT Services
Outsourcing Healthcare IT Services IoT Solutions for Healthcare
IoT Solutions for Healthcare Medical Image Analysis Software Development Services
Medical Image Analysis Software Development Services Lending Software Development Services
Lending Software Development Services Payment Gateway Software Development
Payment Gateway Software Development Accounting Software Development
Accounting Software Development AI-Driven Banking App Development
AI-Driven Banking App Development Insurance Software Development
Insurance Software Development Finance Software Development
Finance Software Development Loan Management Software Development
Loan Management Software Development Decentralized Finance Development Services
Decentralized Finance Development Services eWallet App Development
eWallet App Development Payment App Development
Payment App Development Money Transfer App Development
Money Transfer App Development Mortgage Software Development
Mortgage Software Development Insurance Fraud Detection Software Development
Insurance Fraud Detection Software Development Wealth Management Software Development
Wealth Management Software Development Cryptocurrency Exchange Platform Development
Cryptocurrency Exchange Platform Development Neobank App Development
Neobank App Development Stock Trading App Development
Stock Trading App Development AML software Development
AML software Development Web3 Wallet Development
Web3 Wallet Development Robo-Advisor App Development
Robo-Advisor App Development Supply Chain Management Software Development
Supply Chain Management Software Development Fleet Management Software Development
Fleet Management Software Development Warehouse Management Software Development
Warehouse Management Software Development LMS Development
LMS Development Education App Development
Education App Development Inventory Management Software Development
Inventory Management Software Development Property Management Software Development
Property Management Software Development Real Estate CRM Software Development
Real Estate CRM Software Development Real Estate Document Management Software
Real Estate Document Management Software Construction App Development
Construction App Development Construction ERP Software Development
Construction ERP Software Development





